SDNを用いた大量電子メール攻撃の対策に関する研究
モハマド, ザフラン ビン アブドル アジズ
https://doi.org/10.15017/1931935
出版情報:Kyushu University, 2017, 博士(学術), 課程博士 バージョン:
権利関係:
全文
SDNを用いた大量電子メール攻撃の対策に関する研究
モハマド, ザフラン ビン アブドル アジズ
https://doi.org/10.15017/1931935
出版情報:Kyushu University, 2017, 博士(学術), 課程博士 バージョン:
権利関係:
図
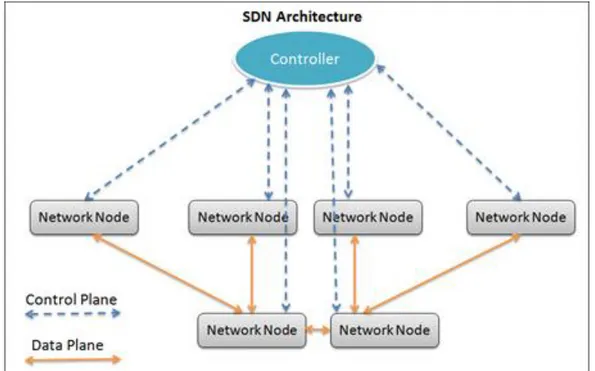
![Figure 1.3 SDN Stacks [9]](https://thumb-ap.123doks.com/thumbv2/123deta/9916749.1918817/32.892.102.791.125.538/figure-sdn-stacks.webp)
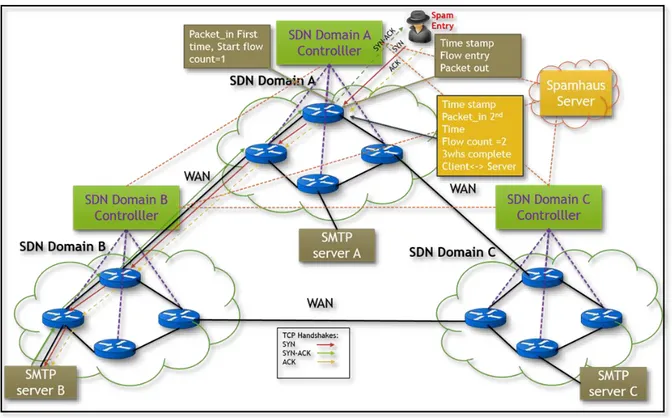
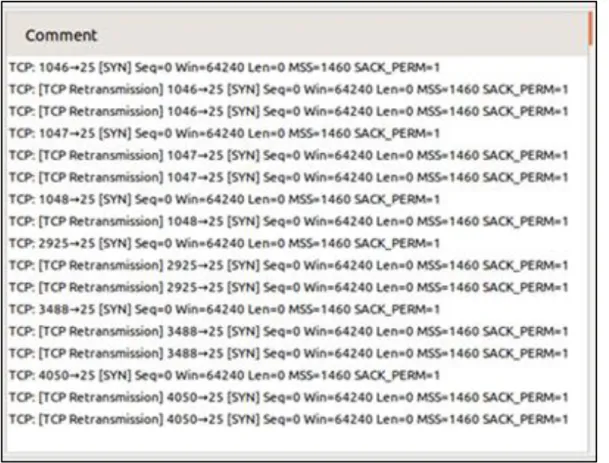
Outline
関連したドキュメント
Department of Cardiovascular and Internal Medicine, Kanazawa University Graduate School of Medicine, Kanazawa (N.F., T.Y., M. Kawashiri, K.H., M.Y.); Department of Pediatrics,
*2 Kanazawa University, Institute of Science and Engineering, Faculty of Geosciences and civil Engineering, Associate Professor. *3 Kanazawa University, Graduate School of
* Department of Mathematical Science, School of Fundamental Science and Engineering, Waseda University, 3‐4‐1 Okubo, Shinjuku, Tokyo 169‐8555, Japan... \mathrm{e}
Arnold This paper deals with recent applications of fractional calculus to dynamical sys- tems in control theory, electrical circuits with fractance, generalized voltage di-
Arnold This paper deals with recent applications of fractional calculus to dynamical sys- tems in control theory, electrical circuits with fractance, generalized voltage di-
(4S) Package ID Vendor ID and packing list number (K) Transit ID Customer's purchase order number (P) Customer Prod ID Customer Part Number. (1P)
Therefore, after the foreign trading vessel departs from a port of loading, the shipping company, who files at the port of loading in the Pre-departure filing (the new rules), will
French case system has a case called tonic in addition to nominative, accusative and dative, and all French nominal SFs appear in tonic forms, regardless of what case their