R377 2017 11 sakuma CS
全文
図
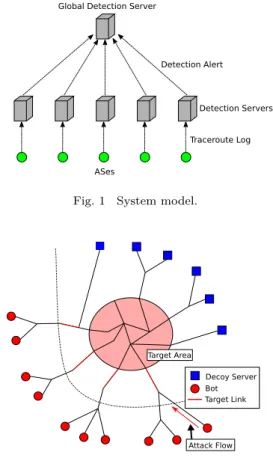
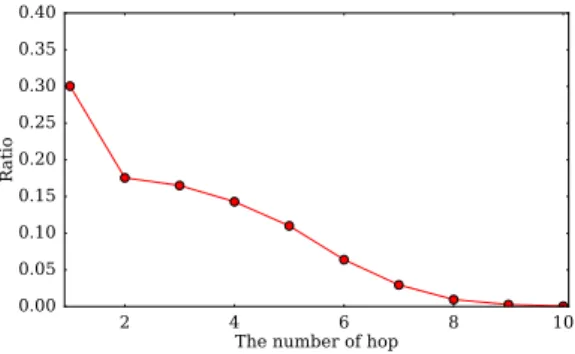
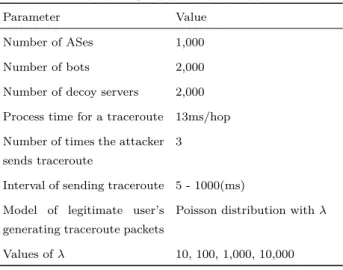

関連したドキュメント
A monotone iteration scheme for traveling waves based on ordered upper and lower solutions is derived for a class of nonlocal dispersal system with delay.. Such system can be used
Since the data measurement work in the Lamb wave-based damage detection is not time consuming, it is reasonable that the density function should be estimated by using robust
In our previous papers, we used the theorems in finite operator calculus to count the number of ballot paths avoiding a given pattern.. From the above example, we see that we have
In the special case of a Boolean algebra, the resulting SJB is orthogonal with respect to the standard inner product and, moreover, we can write down an explicit formula for the
In addition to the basic facts just stated on existence and uniqueness of solutions for our problems, the analysis of the approximation scheme, based on a minimization of the
Khovanov associated to each local move on a link diagram a homomorphism between the homology groups of its source and target diagrams.. In this section we describe how this
Received March 11, 2017, revised September 2017.. The content of our article goes as follows. In the Section 2 we recall a well-known correspondence between A ∞ algebras
Wro ´nski’s construction replaced by phase semantic completion. ASubL3, Crakow 06/11/06