C250 2016 11 WRTLT 最近の更新履歴 Hideo Fujiwara
全文
図
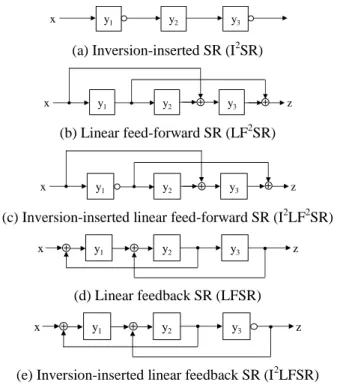
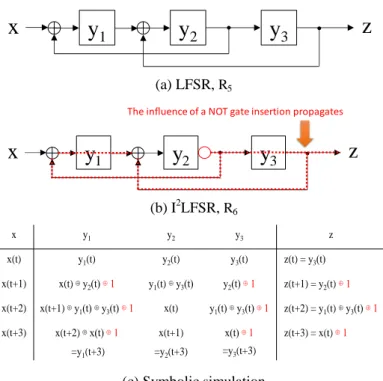
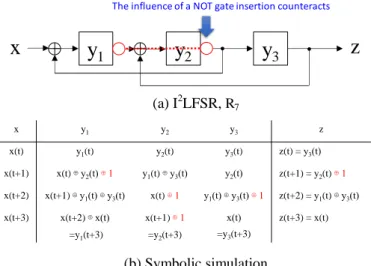
![Figure 4. Design for strongly secure (I 2 )LF 2 SRs states of C the output sequence of length k is always different from that of a k-stage shift register [14]](https://thumb-ap.123doks.com/thumbv2/123deta/5751925.26950/3.893.468.826.89.370/figure-design-strongly-output-sequence-length-different-register.webp)
関連したドキュメント
By employing the theory of topological degree, M -matrix and Lypunov functional, We have obtained some sufficient con- ditions ensuring the existence, uniqueness and global
In this paper, based on a new general ans¨atz and B¨acklund transformation of the fractional Riccati equation with known solutions, we propose a new method called extended
This class of starlike meromorphic functions is developed from Robertson’s concept of star center points [11].. Ma and Minda [7] gave a unified presentation of various subclasses
Since all shift morphisms are bounded sliding block codes in the finite alphabet case, this implies that if K is any field, and if E and F are finite graphs with no sinks and
The predictions of maximum displacement and effective stress of brain under a pressure boundary condition similar to frontal craniotomy but without skull were compared for
Motivated by the new perturbation results of closed linear generalized inverses [12], in this paper, we initiate the study of the following problems for bounded homogeneous
We will for shift spaces having a certain property (∗), show that the first cohomology group is a factor group of Matsumoto’s K 0 -group, and we will also for shift spaces having
The results of the local and remote temperature measurements are stored in the local and remote temperature value registers and are compared with limits programmed into the local