P2P ΫϥυετϨʔδʹ͓͚Δసૹίετݮํ͓ࣜΑͼಗ໊ԽʹΑ
ΔϓϥΠόγอޢํࣜ
ቐɹ૬Ⴣ
†ேൺಸɹܒ
†ɹ
††ܚጯٛक़େֶཧֶ෦ใֶՊ
ԣࢢߓ۠٢ 3-14-1 E-mail: †choi@sasase.ics.keio.ac.jp
͋Β·͠ ۙɺΣϒΫϥυετϨʔδαʔϏεͷधཁ͕ߴ·͍ͬͯΔɻطଘͷΣϒετϨʔδαʔϏεͰɺ αʔόʹશϢʔβσʔλ͕อ͞ΕΔͨΊɺ֎෦͔Βͷ߈ܸʹΑͬͯେྔͷϢʔβσʔλ͕ྲྀग़͢ΔڪΕ͕͋Δɻ͜ Εʹର͠ɺP2P(Peer to Peer) ωοτϫʔΫͷϊʔυΛετϨʔδͱ͠ɺϒϩοΫνΣʔϯʹΑͬͯσʔλͷॴ༗ऀ ͷਖ਼ੑΛอূͨ͠ P2P ΫϥυετϨʔδํ͕ࣜఏҊ͞Ε͍ͯΔ͕ɺଟͷϊʔυΛதܧͯ͠σʔλΛอ͢Δ
͜ͱʹΑΓԆɺτϥώοΫྔͱ͍ͬͨσʔλసૹίετ͕૿Ճ͢Δͱ͍͏՝͕͋Δɻ·ͨɺϒϩοΫνΣʔϯ શϊʔυ͕ӾཡͰ͖ΔͨΊσʔλͷॴ༗ऀͳͲϢʔβͷϓϥΠόγʔ͕৵͞ΕΔڪΕ͕͋Δɻͦ͜ͰຊจͰɺ σʔλͷมߋසʹجͮ͘ετϨʔδϊʔυબ๏͓ΑͼϥϯμϜʹબͨ͠ϦϨʔϊʔυΛϓϩΩγͱͯ͠༻͍ͯ ૹ৴ऀΛಗ໊Խ͢Δ͜ͱʹΑΔϓϥΠόγΛอޢͷํࣜΛఏҊ͢ΔɻγϛϡϨʔγϣϯධՁʹΑΓɺఏҊํ͕ࣜैདྷ
ํࣜͱൺσʔλసૹίετ͕ݮͨ͜͠ͱɺϢʔβͷϓϥΠόγΛޮՌతʹอޢͰ͖Δ͜ͱΛࣔ͢ɻ Ωʔϫʔυ P2P ετϨʔδɺΫϥυετϨʔδɺϒϩοΫνΣʔϯ
Low Transmission Cost P2P Storage Scheme with Privacy Protection
Sanghun CHOI
†, Hiromu ASAHINA
†, and Iwao SASASE
††Dept. of Information and Computer Science, Keio University 3-14-1 Hiyoshi, Kohoku, Yokohama, Kanagawa 223-8522, Japan
E-mail: †choi@sasase.ics.keio.ac.jp
Abstract Although the WCS(Web Cloud Storage) Services are quite convenient and usually used these days, there is a problem that the storage server cloud be targeted by the attacker. To safely store the user’s data without the central server, the P2P(Peer to Peer) storage methods have been studied. Even though the P2P storage relieves the risk of attacks, these have two challenges: reducing the transmission and the delay which are the fundamental problems of P2P, and preventing the user’s privacy from the malicious nodes which store the user’s data. In this paper, in order to solve these challenges mentioned above, we propose an efficient P2P storage scheme with privacy protection. The main ideas of our scheme are that the storage nodes are selected according to the updating frequency of data for reducing the transmission and the delay, and the relay nodes can be acted as the owners of data instead of the real owner of data for protecting the user’s privacy. Furthermore, by using the DIFF method which generates the difference between two data, the user can effectively modify the stored data with the lower transmission and delay. We demonstrate the reduction of the transmission and the delay, and the privacy protection by the computer simulation.
Key words P2P storage, Cloud storage, Blockchain.
1. Introduction
In these days, with the growth of the network and the portable devices, many people can easily access to the Inter-
net and enjoy a lot of internet services. One of the most pop- ular services is the WCS(Web Cloud Storage) service such as Google Drive [1] and Drop Box [2]. If a user accesses to the Internet by its own devices, the user can save new data and
― 15 ―
This article is a technical report without peer review, and its polished and/or extended version may be published elsewhere. 一般社団法人 電子情報通信学会 信学技報
THE I NSTI TUTE OF ELECTRONI CS, I EI CE Tec hni c al Repor t I NFORMATI ON AND COMMUNI CATI ON ENGI NEERS CS2017- 57 ( 2017- 11)
modify the data anytime and anywhere by saving the data to the WCS. However, it is impossible to guarantee the user’s privacy. Firstly, since the attacker can easily detect the tar- get server, the user’s data is always exposed to a risk of the attacks. Secondly, the WCS itself can become an attacker who utilizes the user’s data without the agreement. To solve these problems, the schemes which encrypt the user’s data have been proposed [3] − [5]. However, since these still adopt the central server, they have a risk of the undefeatable attack anytime [6].
To store the user’s data without the central server, Peer to Peer(P2P) storage methods have been investigated [7] − [9]. The P2P storage can provide the same usability as the WCS does while relieving the difficulty of privacy protection. The user’s data are encrypted and divided into multiple pieces and stored in free space of the storage nodes and the au- thority of the data is guaranteed by the blockchain which records all history of data transfers. Since the node except the owner of data cannot obtain all the pieces of data, the privacy protection in the P2P storage scheme is easier than that of the WCS. Also, the user can restore the lost data from the storage nodes through the error correction, even though some storage nodes and the user’s data are lost. Fur- thermore, the P2P storage’s storage space is able to get lager than the WCS. According to the P2P scheme [10], if the users of the whole world begin to share the storage space on their devices for using the P2P storage, the P2P storage can have the storage space of 250,000 PB. Compared to the Google Drive which recently has the storage space of 8,000 PB, the P2P storage’s space is much lager. To prove the reliabil- ity of the P2P storage scheme, the blockchain is adopted [9]. By using the blockchain, every storage node in P2P network checks each other whether other storage nodes safely stored the user’s data. If the user’s data are damaged or changed, every storage node can detect this and share the malicious situation in the P2P network. Despite of these advantages, there are two agendas to be considered. First, the communi- cation cost of the user which is the number of transmission and the delay for exchanging is high. Since the user ran- domly selects the storage nodes in the P2P network, some of the user’s divided data might be saved in the distant storage nodes. This causes the high communication cost. Second, there is still the possibility of the attacks. Since all nodes in the network can trace the data transfers, an attacker can nar- row the target nodes which store the specific user’s data [11]. In this paper, in order to develop the P2P storage scheme mentioned above, we propose an efficient P2P storage scheme with privacy protection. To improve the first agenda, the user selects the closest storage nodes based on the updating frequency which is the rate how often the user reads and
modifies the data. Since a user can obtain the data which is often accessed with low delay and few transmissions, the average communication cost is reduced. In order to reduce the communication cost further, the methods called DIF F which generates the script for converting an old data to a new data is adopted when the user tries to modify the stored data in the storage nodes. As the second agenda, to prevent the owner of the data and the user’s privacy from being identified by tracing the blockchain, the randomly selected relay nodes are recorded as the owner of the data in the blockchain in the P2P storage.
The rest of this paper is constructed as the follows. Section 2. describes the system model. The related work is intro- duced in Section 3.. The proposed scheme is described in Section 4.. The analysis and the results are shown in Section 5.. Finally, we conclude our research in 6..
2. P2P Storage
2. 1 Blockchain
The blockchain is a digital ledger in which transactions are made in bitcoin scheme for protecting the nodes and detect- ing the malicious nodes [14]. For operating the blockchain in the P2P storage scheme, the user shares the block includ- ing the user’s data list and the storage nodes which have the user’s data to the P2P network. Because this block is connected like the chain and it records the flow of the data with the agreement of all nodes, the user’s data are safely stored in the storage nodes in the P2P network. Also, any node cannot harm the data because all nodes can detect the malicious situation such as the abnormal modification of the data. Through the blockchain, all of the nodes can know the user’s information included in the block.
3. Related work
3. 1 Cloud storage with the edge computing To reduce the overload of the cloud central server, the edge computing schemes have been proposed [4], [5]. The edge computer is the distributed information technology architec- ture in which client data are processed at the periphery of the network as closest to the originating source as possible. According to the user’s preference of the data such as the movie, the preferred data will be stored in the edge com- puter nearby the user. Therefore, the user accesses to the closest edge computer, not to the cloud central server, to utilize the data. This is able to reduce the communication cost as the overload. However, if user’s preference of the data is changed and the number of the users becomes large, the communication cost will be increased. Moreover, the many edge computers are required to cover many users. To over- come this problem, the P2P storage schemes are suggested
as below.
3. 2 P2P storage scheme
To maintain the P2P storage scheme, the user who is the one of nodes in the P2P network shares some space via the Internet [7] − [9]. The user can store the data in the storage nodes in P2P network regardless of the server. In addition, the use can access to the P2P storage without any restric- tion as the P2P storage is composed of many users. For storing the data in the storage nodes, first the user divides the data into some pieces of data. The user encrypts di- vided data by using the secret key. Secondly, to store the encrypted data to the nodes in the P2P network the user randomly selects the nodes to be the storage nodes whose number is equal to that of the divided data. In this case, the user’s data might be located in the distant nodes. When the user wants to modify the data, the user receives the di- vided data from the storage nodes. Then, the user decrypts them and combines them into the one original data. After converting the original data, the user divides the data and encrypts them again. The divided data are stored in the storage nodes again. To improve P2P storage scheme, the blockchain method is adopted [9]. Through the P2P storage with the blockchain, the user’s data are safely stored in the storage nodes. The storage nodes cannot try to change the user’s data at their will, because the blockchain system de- tects it. Despite of this advantage, there are two points to improve. Firstly, the communication cost of the user which is the transmission time and the delay of the exchanging data in the network is high when the user stores the data and reads the stored data for modifying from the distant storage nodes. Secondly, the user’s privacy can not be guaranteed. Because all of the storage nodes can know who is the owner of stored data via the blockchain method. If Bob who is the real user stores the data in the storage nodes: S1, S2 and S3, he will share the block, including the user’s data list and the storage nodes which have the user’s data, to all of the nodes in the P2P network. Then, the storage nodes S1, S2, and S3 can know that they have Bob’s data. Therefore, they are possible to decode the Bob’s data.
3. 3 Modification with the difference of data To modify the data with the small data size, the schemes which modify the data by using DIF F , the difference be- tween the original data and modified data, have been pro- posed [12], [13]. DIF F can adopt all of the data types since the data are composed of the binary ones. Also, DIF F can be extracted from the encrypted data. By using DIF F , the data are effectively modified. For example, if DIF F is gen- erated between A which is the original one and B which is the modified one, C which is the copied one from A can ob- tain B by using DIF F . To adopt this to the data storage
scheme, the user can change the stored data by using DIF F without sending the modified data to the storage.
4. Proposed Scheme
In order to overcome the shortcomings mentioned in Sec- tion III, we propose the efficient P2P storage scheme with privacy protection. The main idea of our scheme is classified into three categories. Firstly, to reduce the communication cost when the user stores the data in storage nodes, the clos- est storage nodes in P2P network are selected by the differ- ence of the updating frequency of the data. The updating frequency is the rate how often the user reads and modifies the data. Secondly, to reduce the communication cost when the user modifies the stored data, DIFF method is utilized. Thirdly, to ensure the user’s privacy from the storage nodes in the blockchain, the random relay nodes pretend to be the owner of the data instead of the real user. In our proposed P2P storage scheme, the user can safely use the P2P storage with the low communication cost and the guarantee of the privacy.
4. 1 Selection of the closest storage nodes
Here, to reduce the user’s communication cost when the user wants to store the data, the user chooses the closest storage nodes by the difference of updating frequency, which is the rate how often the user reads and modifies the data, of the data. Then, the user makes the policy of updating frequency of the data as shown in Table I-(a) and checks the state of all nodes in Table I-(b) before storing the data to the storage nodes. The user can set the updating frequency of the data and the policy of the updating frequency how to work in the P2P storage before storing the data to the storage nodes. Also, the updating frequency of stored data in the storage nodes is arranged by the user. In this step, the variables are defined as: D is the user’s data which will be stored in the storage nodes, L is the list of all of the storage nodes in P2P network, T is the close storage nodes which is chosen from L, S is the number of close storage nodes which the user’s data will be stored and the data to be divided. First, the user inspects the updating frequency of D in the policy as shown in Table I-(a). If D’s updating frequency has been set high, the user selects T . Then, the user divides and encrypts D by the user’s secret key as the number of S. Finally, the user sends D to T .
4. 1. 1 Exchanging the storage nodes
In this step, if the updating frequency of the stored data is changed in the storage nodes, the stored data’s storage nodes are will be exchanged. For example, if the document frequency becomes to be low or the video frequency becomes to be high, the data’s storage nodes are exchanged. The doc- ument data will be replaced in the distant storage nodes. On
ද1: Initialization of the user
(a) Updating Frequency
High Low Document Audio
Image Video Graphic Record
... ...
(b) List of the nodes in P2P
Node Hop M/S Capacity(GB)
1 1 2 20
2 2 10 10
... ... ... ...
n n n n
the other hand, the video data will be replaced in the closest storage nodes.
4. 2 Modification of the data with the low cost To reduce the communication cost when the user wants to modify the stored data in the P2P storage scheme, we take note of DIF F method. In the conventional scheme, the user has to receive all of the stored data from the stor- age nodes for modification and resends the modified data to store. This causes the high communication cost due to the exchanging data in the network. On the other hand, in the proposed scheme the user can effectively modify the stored data with the low communication cost through DIF F meth- ods. DIF F methods are the following two cases.
4. 2. 1 Modification with the original data in the user’s devices.
In this step, if the original data is kept in the user’s device, the user is not necessary to receive all of the divided-stored data from the storage nodes for modifying the stored data. We assume that A is the original one, B is the modified data, C is the stored data in the storage nodes, and D is DIF F which is the difference between A and B. In the con- ventional scheme, after generating B the user divides and encrypts B to store in the storage nodes. However, in the proposed scheme, the user does not need to send the divided B to the storage nodes. By DIF F methods, after generat- ing B the user makes D between A and B and sends D to the storage nodes to modify C. The number of D as same as the number of C. For example, if the number of stored data in storage nodes are three, the user has to divide the original data and the modified data into three divided ones. And the user sends D to the storage nodes. Then, by using D, the storage nodes can change C to B. In the proposed scheme, the user does not need to send all of divided B to the storage nodes. The user only sends D to the storage nodes. Therefore, the user can effectively modify the stored data in storage nodes by using DIF F .
4. 2. 2 Modification without the original data in the user’s devices
If the user does not have the original data in the device, the user needs to receive all of the divided-stored data from
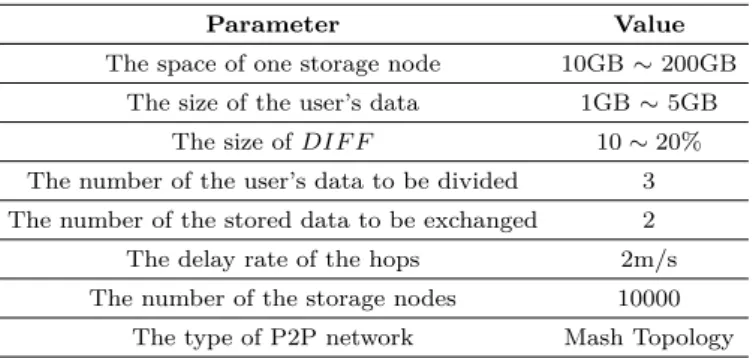
ද2: Simulation parameters
Parameter Value
The space of one storage node 10GB ∼ 200GB The size of the user’s data 1GB ∼ 5GB
The size of DIF F 10 ∼ 20%
The number of the user’s data to be divided 3 The number of the stored data to be exchanged 2 The delay rate of the hops 2m/s The number of the storage nodes 10000
The type of P2P network Mash Topology
ද3: Average hop per user in P2P
Hop 1 2 3 4 5 6 7 8 9
Node 1 7 89 870 3779 4228 1551 137 9
the storage nodes are similar to the conventional scheme for the modification. The user restores the divided-stored data into the one original data. Then, the user starts to modify the original data. After modifying the data, the user follows the same process mentioned above 4.2.1.
5. Analysis And Result
Our analytical method has two purposes: Fist purpose is that the comparison of the communication cost between the conventional scheme [9], and our proposed scheme with 4 cases, Second purpose is that the protection of the user’s pri- vacy from the malicious storage nodes in the blockchain. To compare the communication cost between the conventional scheme and our proposed scheme, the data set of Gnutella P2P network is adopted [15]. Gnutella is a decentralized P2P network that allows users to share data via the Internet without the central server. The parameter of the simulation is shown in Table II. The average hops per user in this data set is shown in Table III. This analysis is carried by increasing 500 nodes from 1000 nodes to 10000 nodes by the MATLAB.
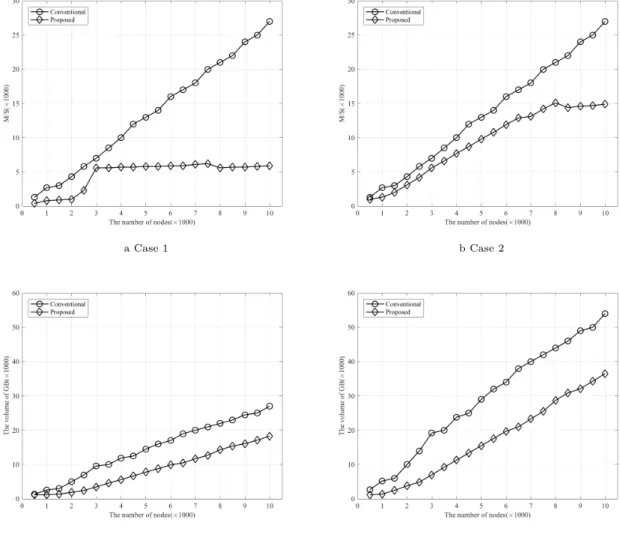
5. 1 Case 1
Fig. 1-(a) shows the comparison of the communication cost of the delay rate of hops in the P2P storage scheme when the user sends data to the storage nodes. It is shown that our proposed scheme’s cost is lower than the conven- tional scheme. The user sends three data to the storage nodes in both schemes as shown in Table II. In the conven- tional scheme, the user randomly selects the storage nodes three times in the range shown in Table III. In our proposed scheme, the user chooses the closest storage nodes three times by considering the updating frequency. Also, if the space of the closest storage nodes is full, the user stores the data in the next hop’s storage nodes. Therefore, the delay due to hop in the P2P storage will be changed. In the proposed scheme, the cost is rapidly increasing from 2000 users be-
a Case 1 b Case 2
c Case 3 d Case 4
ਤ1: Comparison of the communication cost
cause the space of the storage nodes is full in range of 1∼2 hops. So, the user needs to store the data to the storage nodes of 3 hops. The cost is increasing little by little from 2500 to 8000 users because the user’s data can be stored in the storage nodes in range of 5 hops. In addition, the cost is decreasing from 8000 users, the user’s data can be stored in the storage nodes in the range of 4 hops.
5. 2 Case 2
This part reflects the additional cost to the case 1. In the proposed scheme, we assume that the two storage nodes are exchanged according to change in the updating frequency of the two data as shown in Table II. The communication cost of the conventional scheme is as same as the case 1. In the pro- posed scheme, the communication cost of the transmission delay is generated from exchanging the storage nodes when the updating frequency of the data is changed by the user. The storage nodes are exchanged two times in the range of Table III since the user’s data which will be exchanged in the storage nodes are two. Fig. 1-(b) shows that our proposed scheme’s cost is lower than the conventional scheme despite
of the additional process of exchanging the storage nodes. Because the closest storage nodes are selected by the policy of the updating frequency when the user stores the data to the storage nodes for the first time.
5. 3 Case 3
Fig. 1-(c) shows the comparison of the communication cost generated from the size of exchanging the data when the user modifies the stored data. Here, we assumes the user has the original data in the user’s devices. A is the original one, B is the modified data, C is the stored data in the storage nodes and D is DIF F which is the difference between A and B. In the conventional scheme, after generating B, the user di- vides and encrypts B to store in the storage nodes. Then, the user has to send the divided B to the storage nodes to store. However, in the proposed scheme, the user does not need to send the divided B to the storage nodes. The user only sends D to the storage nodes. We assume the size of D is 10 ∼ 20% of B by the experiment. Therefore, in our pro- posed scheme, the communication cost is much lower than the conventional scheme.
5. 4 Case 4
Fig. 1-(d) shows another comparison of the communica- tion cost generated from the size of exchanging data when the user modifies the stored data. Here, it is assumed that the user has not the original data in the user’s devices. It re- flects the additional cost, which is the size of receiving data from the storage nodes, to the case 3. After receiving all of the stored data from the storage nodes, the user has to restore them to the original one in both schemes. Also, by using the original one, the user modifies the data. But, as we mentioned above, the sending cost is different, because the user only sends the size of DIF F to the storage nodes. Therefore, our proposed scheme’s cost will be lower than the conventional scheme.
Through these analysis, we can show that the user can use the P2P storage scheme with the low communication cost in our proposed scheme.
5. 5 The protection of the user’s privacy
To protect the user’s privacy in the blockchian in the P2P storage scheme, the relay nodes are adopted in our proposed scheme. The relay nodes are the mediators between the user and the storage nodes. In the conventional scheme, the user’s privacy is leaked from the malicious storage nodes in the blockchain. However, in our proposed scheme by using the relay nodes the user’s data will be protected from the the malicious nodes in the blockchain. For this, firstly the user selects the storage nodes: S1, S2 and S3, and chooses the relay nodes: R1, R2 and R3. If the user’s data are divided and encrypted into three, the user sends each data to R1, R2 and R3 respectively. The number of relay nodes as same as the storage nodes. R1, R2 and R3 know the owner of the data, but they can not inspect whether the other relay nodes have received the data from the same user. They will be the owner of data on behalf of the user. And they send the data to the storage nodes: S1, S2 and S3. After the data are stored in the storage nodes, S1, S2 and S3 generate the block one by one and share the block to the blockchain in P2P network. Then, S1, S2 and S3 will recognize R1, R2 and R3 as the owner of the data, not the real user. The user’s data will be safe from the storage nodes. Therefore, if the storage nodes and the relay nodes are malicious, they cannot get the user’s data since they cannot know the real owner of the data despite the blockchain scheme is adopted in our scheme. Also, the the relay nodes cannot damage the user’s data while mediating. Because, if the relay nodes damage the user’s data at will, the user can know this situ- ation through the block which is made by relay nodes in the blockchain. Moreover, the relay nodes and the storage nodes cannot conspire in order to obtain the user’s data. Because the user’s data are divided one by one respectively in P2P
network, they only have one piece of the user’s whole data. Through this process, the user can safely maintain and use the P2P storage scheme with the protection of user’s privacy in the blockchain.
6. Conclusion
To reduce the communication cost and protect the user’s privacy in the P2P storage scheme by using the blockchain, we have proposed the efficient P2P storage scheme with pri- vacy protection. By selecting the storage nodes according to the updating frequency of the data, the communication cost is reduced. Furthermore, the user’s privacy is protected from the storage nodes through the relay nodes in the blockchain. In our proposed scheme, the user can safely use the P2P storage with the low cost.
7. Acknowledgment
This work is partly supported by the Grant in Aid forɹ Scientific Research (No.17K06440) from Japan Society for Promotion of Science (JSPS).
จ ݙ
[1] Quick, D., Choo, K. K. R. (2014). Google drive: Forensic analysis of data remnants. Journal of Network and Com- puter Applications, 40(1), 179-193.
[2] Drago, I., Mellia, M., M. Munafo, M., Sperotto, A., Sadre, R., Pras, A. (2012). Inside dropbox. Proceedings of the 2012 ACM Conference on Internet Measurement Conference - IMC ’12, 481.
[3] Zhang, J., Zhang, Z., Guo, H. (2017). Towards Secure Data Distribution Systems in Mobile Cloud Computing. IEEE Transactions on Mobile Computing, 1233(c), 1-1.
[4] Ahmed, A., Ahmed, A., Ahmed, E. (2016). A Survey on Mobile Edge Computing A Survey on Mobile Edge Com- puting.
[5] Satya, M. S. (2016). Edge Computing:Vision and Chal- lenges, 3(5), 637-646.
[6] P. Ducklin, Anatomy of a Password disaster - Adobe’s giant- sized Cryptographic Blunder,Naked Security, 2013. [7] Jacob, F., Mittag, J., Hartenstein, H. (2015). A security
analysis of the emerging P2P-based personal cloud plat- form MaidSafe. Proceedings - 14th IEEE International Con- ference on Trust, Security and Privacy in Computing and Communications, TrustCom 2015, 1, 1403-1410.
[8] ÃĎÃňFr, C., Mazauric, D., St, J. M. (2014). P2P storage systems: Study of different placement policies, 427-443. [9] Wilkinson, S. (2014). Storj A Peer-to-Peer Cloud Storage
Network Files as Encrypted Shards, 1-18. Retrieved from https://storj.io/storj.pdf.
[10] How big is the cloudclosest, (2014).
[11] Z. Lin, A Large-Scale Study of Web Password Habits of Chinese Network Users, Journal of Software, vol. 9, no. 2, pp. 293-297, 2014.
[12] Mackenzie, D., Eggert, P., Stallman, R. (2002). Comparing and Merging Files with GNU diff and patch. Differences. [13] Blischak, J. D., Davenport, E. R., Wilson, G. (2016).
A Quick Introduction to Version Control with Git and GitHub. PLoS Computational Biology, 12(1), 1-18. [14] S. Nakamoto. Bitcoin: A peer-to-peer electronic cash sys-
tem, (2009). https://bitcoin.org/bitcoin.pdf.
[15] https://snap.stanford.edu/data/p2p-Gnutella04.html.